Detection of ZeroLogon (CVE-2020-1472) using SensorFleet
Posted 21 Sep 2020
Introduction
ZeroLogon can be used to exploit a serious vulnerability in Windows Domain Controllers.
I was recently asked if you could detect a ZeroLogon attempt using a SensorFleet-based Sensor. It is easy because we have plug & play support for Emerging Threats intrusion detection ruleset and ZeroLogon was added to the ruleset on September 14th 2020.
Emerging Threats can be enabled in our IDS Rule Manager- and Suricata IDS Instruments.
Here’s how you do it. We’re going to assume that basic Sensor configuration is already done.
Step 1: Install Rule Manager and Suricata
There are few easy steps to take if you don’t have IDS Rule Manager and Suricata IDS already enabled:
- Navigate to SensorFleet Fleet Management UI
-
Choose your target Sensor, and choose Add Instrument from the dropdown menu
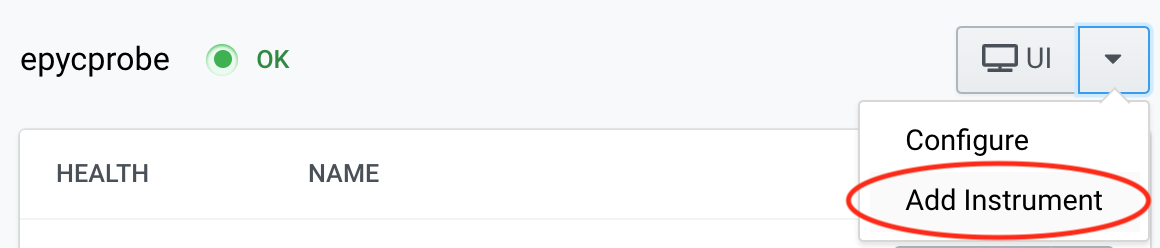
-
Click Add instrument for Suricata and IDS Rule Manager
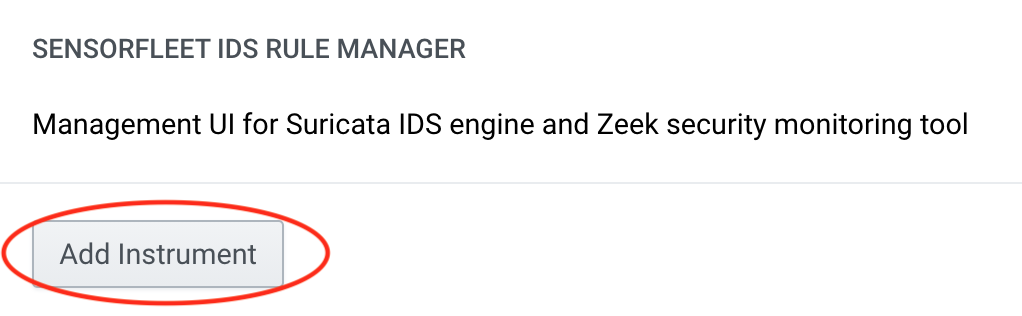
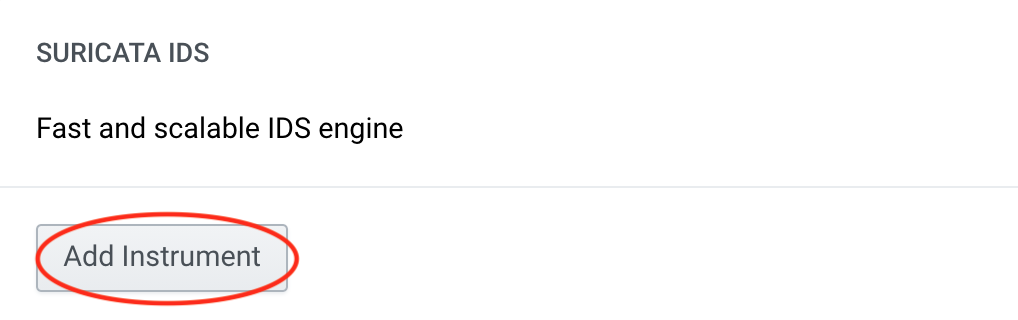
Step 2: Configure a capture interface for Suricata
Even if you don’t have it already done, setting up traffic monitoring is a breeze. It is enough to choose the capture interface since SensorFleet Capture Engine is usually already configured as part of standard Sensor configuration.
-
Locate Suricata IDS from your Fleet Management UI and choose Configure from the dropdown menu (it might display an error status due to missing capture interface - that’s normal).
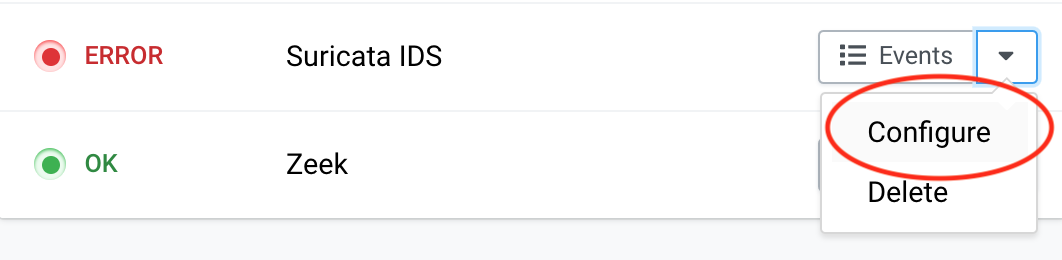
-
Choose Add Interface, select Sensor bridge, type some interface name, only choose capability RX and hit Create.
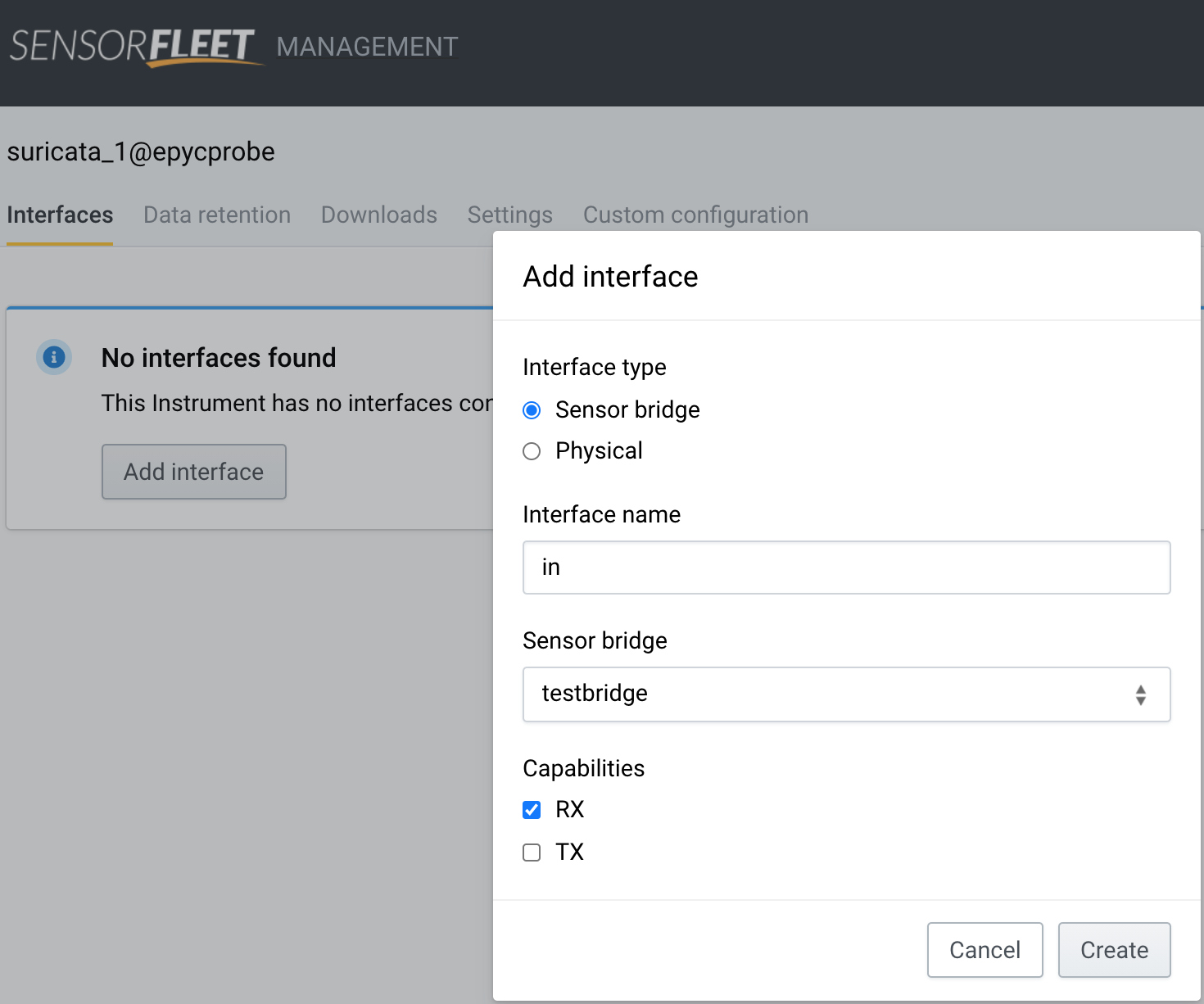
-
Suricata status will change to OK after the configuration:

Step 3: Add Emerging Threats ruleset
Downloader Instrument is enabled as part of standard Sensor configuration and it gives you a centrally controlled way to fetch external configuration, such as the Emerging Threats ruleset. You just need to add a new source and the Downloader will do the heavy lifting.
-
Locate IDS Rule Manager Instrument from Fleet Management UI and click the UI button

-
Click Add rulesource
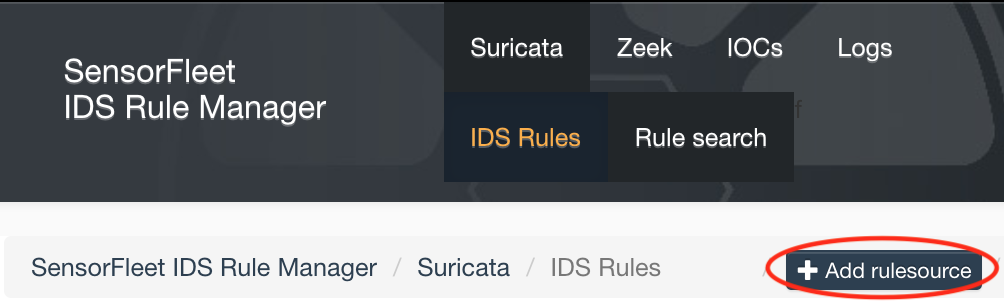
-
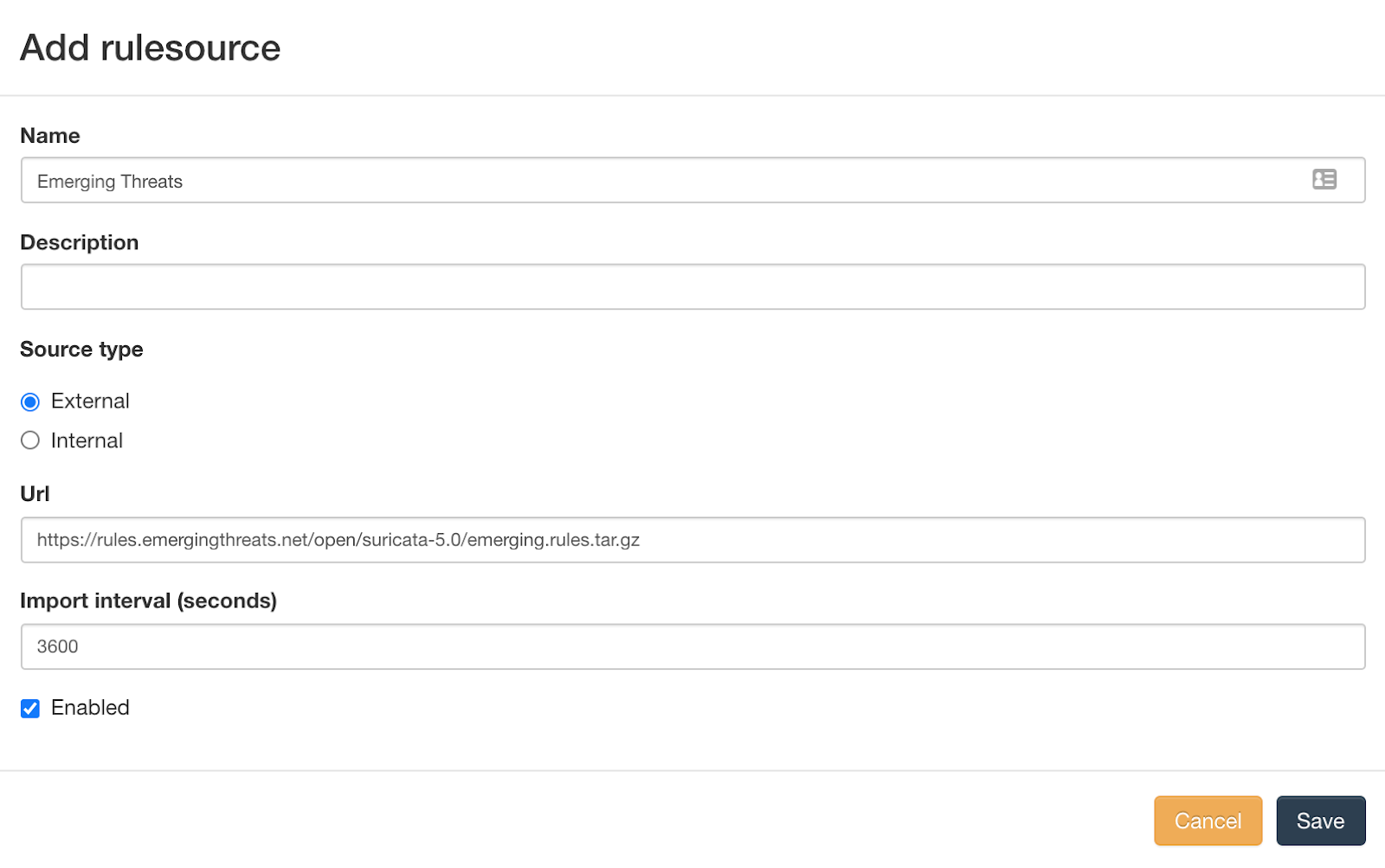
Type settings for the rulesource:
Name: Emerging Threats URL: https://rules.emergingthreats.net/open/suricata-5.0/emerging.rules.tar.gz Source type: External Import Interval: 3600 [X] EnabledWith these settings, the URL will be checked for updates with HTTP HEAD every 3600 seconds, and downloaded only when file changes.
-
After a while, you will see the Emerging Threats rules in Rule Manager UI.
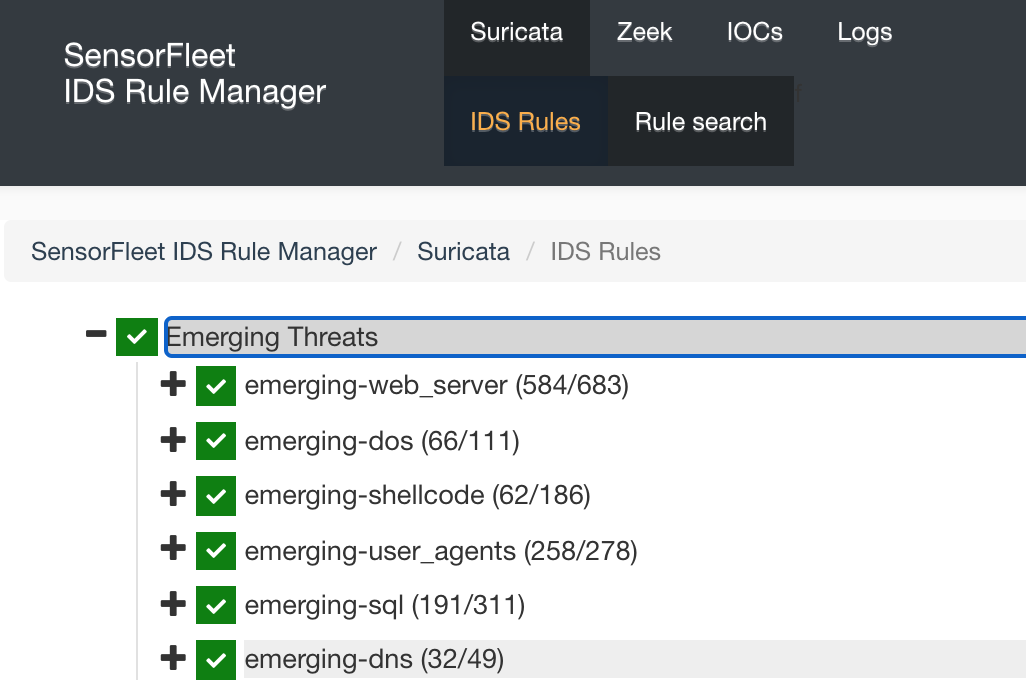
-
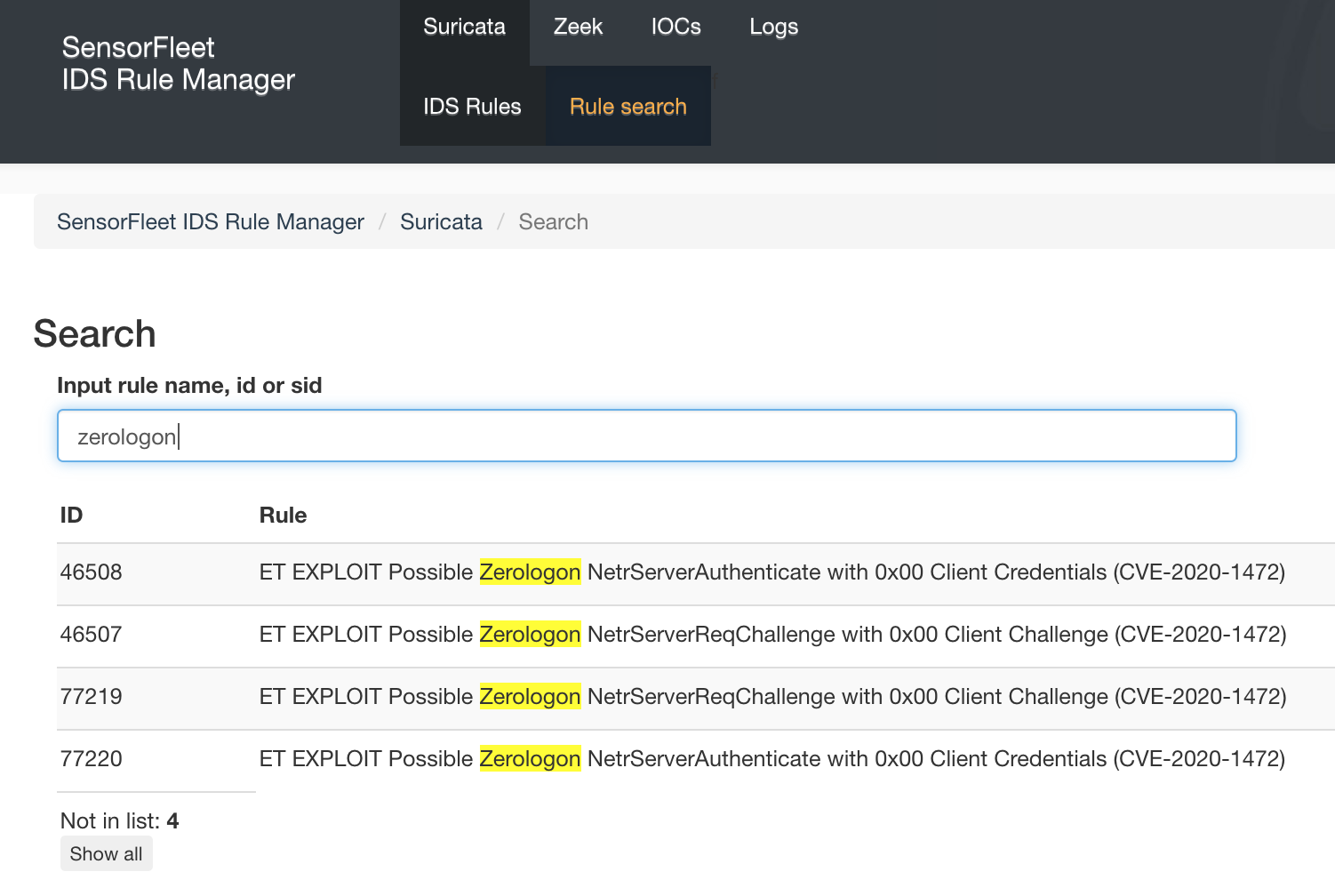
Just in case, you can search the ruleset to find the ZeroLogon Rule. Open Rule search and type zerologon to show the zerologon rules.
Step 4: Testing the rule
It is always a good idea to test your ruleset.
Right now, the easiest way to test it against ZeroLogon detection would be to replay a traffic capture (pcap) that should trigger the alert. Luckily there is a pcap that does just this.
There is another way - launch a live attack against your Windows Domain Controller. I wouldn’t try that in production though.
We’re going to try the pcap. This assumes you only have a single bridge in your setup.
- Login to your sensor using SSH.
-
List active bridges:
fleet config show <sensor_id> -
Install tcpreplay utility:
sudo apt update && sudo apt install tcpreplay - Grant permissions to write to the bridge interface from host.
cat > /etc/ferm/ferm.d/99-allow-br0-hostbridge.conf <<EOF domain eb chain INPUT logical-in br0 ACCEPT; domain eb chain OUTPUT logical-out br0 ACCEPT; EOF service ferm reload - Download the test pcap to your sensor.
curl \ https://github.com/corelight/zerologon/blob/master/testing/Traces/CVE-2020-1472_exploit_win2019.pcap \ -o /root/zerologon.pcap -
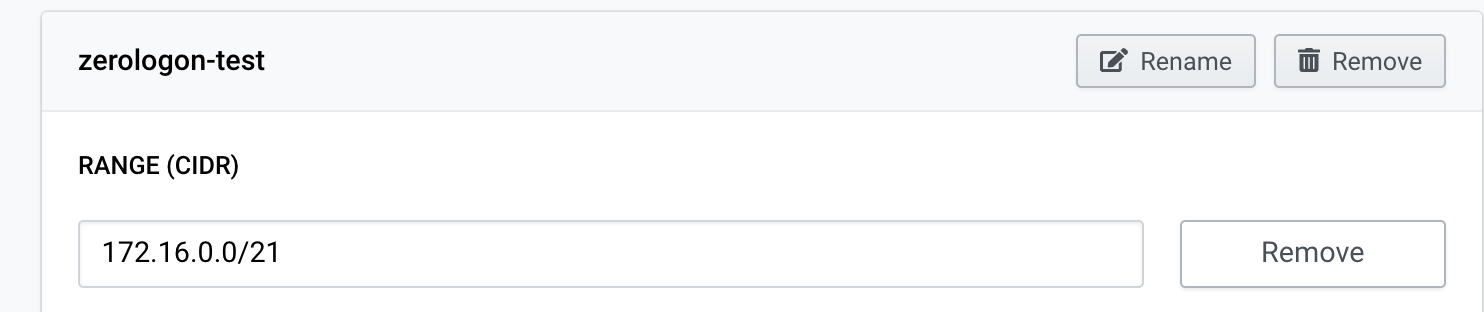
The exploit in pcap uses the IP addresses 172.16.0.10 and 172.16.5.58. Those should be included in your Sensor’s homenets. Add 172.16.0.0/21 to your Sensor homenets: Choose configure from the Sensor dropdown menu, open Settings tab, add home network 172.16.0.0/21 and Save.
-
Replay the pcap file to your bridge interface
tcpreplay-edit -i br0 /root/zerologon.pcap -
Open Suricata IDS events page. You should see events like these:
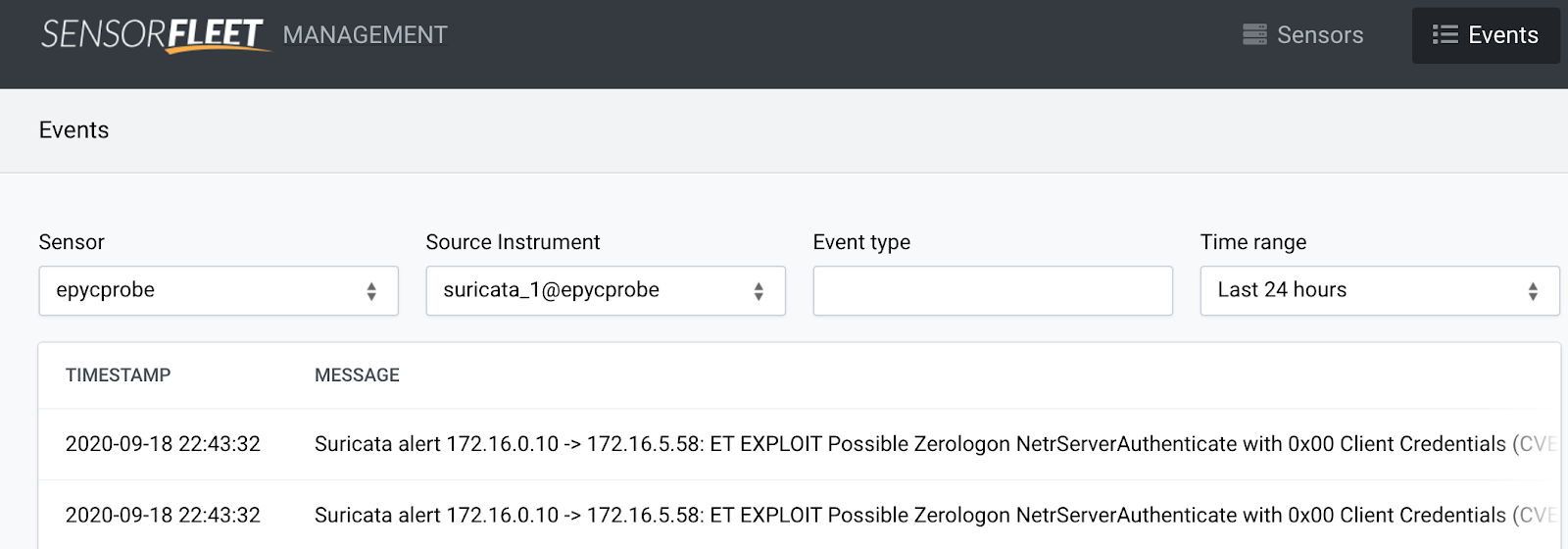
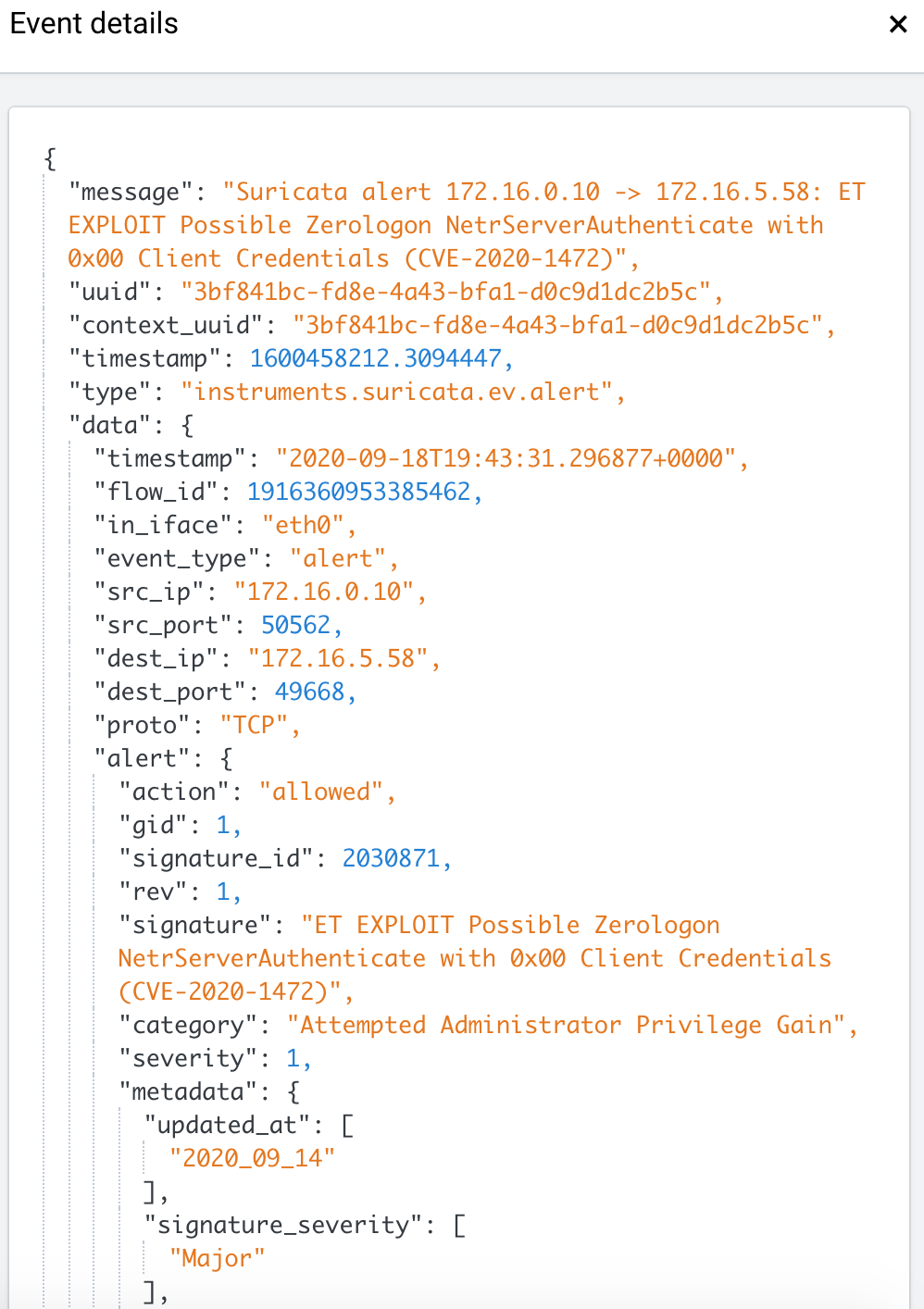
Event message: Suricata alert 172.16.0.10 -> 172.16.5.58: ET EXPLOIT Possible Zerologon NetrServerAuthenticate with 0x00 Client Credentials (CVE-2020-1472)
Final words
Running Suricata in your network can be very useful. With good quality free rules like Emerging Threats, you can catch a lot of badness in your network before things get out of control. If you see such an event, there might be still time to shutdown or disconnect the servers and create last minute snapshots of the data before the attacker installs a cryptolocker software or some other means to disrupt your business.
